What is SMB?

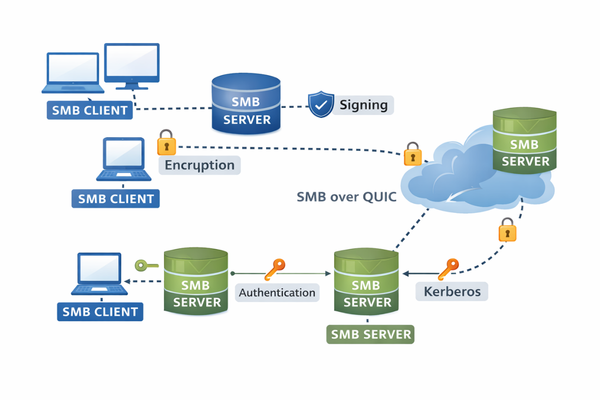
SMB is a network file and resource sharing protocol that uses a client-server model. SMB clients such as PCs on a network connect to SMB servers to access resources such as files and directories or perform tasks like printing over the network.
Often, the term CIFS — short for Common Internet File System — is used interchangeably with Server Message Block. That is because CIFS was a popular Microsoft SMB implementation introduced with Windows 95. Since then, the informal use of CIFS to refer to SMB has remained common.
How SMB Works?
At a high level, SMB communication is easy to understand. SMB clients connect to an SMB server using the SMB port to access SMB shares. Once they access the SMB shares, clients can do things such as collaborate on files without downloading them to their machines or print using a networked printer.
What is an SMB Client?
An SMB client is the device that accesses resources on an SMB server. For example, within a corporate network, the user PCs that access a shared drive are SMB clients.
What is an SMB Server?
An SMB server is the network server — or cluster of servers — where SMB shares are stored. The SMB server grants or denies SMB clients access to the shared resources (a.k.a. SMB shares).
What is an SMB Share?
An SMB share, also known as an SMB file share, is simply a shared resource on an SMB server. Often, an SMB share is a directory, but it can be any shared resource. For example, network printers are often shared using Server Message Block.
What is an SMB Port?
By default, modern implementations of SMB use TCP port 445 as the SMB port. Older SMB implementations (pre-Windows 2000) used SMB port 139.
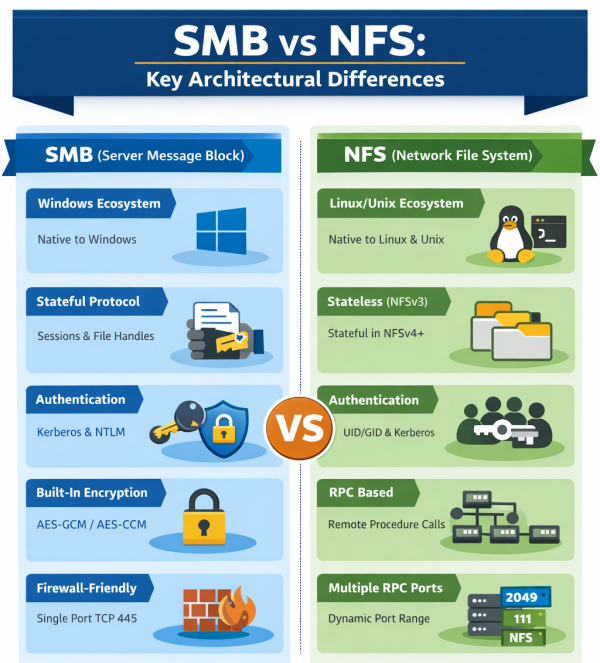
Versions of SMB: Understanding SMB v1, SMB v2, and SMB v3
SMB v1 (SMB1)- The original Server Message Block version. SMB1 began in the 1980s and has gone through multiple iterations. In Windows 95, Microsoft introduced CIFS as a way to implement SMB1. In modern applications, you should NOT use SMB v1 because it is insecure (no encryption, has been exploited in attacks like WannaCry and NotPetya) and inefficient (very “chatty” on networks creating congestion and reduced performance).
SMB v2 (SMB2)- SMB2 was introduced with Windows Vista. This version of SMB had significant improvements in performance and simplicity when compared to SMB1. Additionally, SMBv2 offered security enhancements. For example, SMB2.0.2 introduced pre-authentication integrity and SMB2 is not vulnerable to the same WannaCry and NotPeyta exploits that make SMB1 a security risk. SMB v2.1 was introduced with Windows 7 and Server 2008 R2, further improving performance and oplocks (opportunistic locking).
SMB v3 (SMB3)- SMB3 introduced end-to-end SMB encryption and, later, the most advanced and secure implementations of SMB. The first release of SMB3 (a.k.a. SMB v3.0) came with Windows 8 and Server 2012. SMB v3.02 was introduced in Windows 8.1 and Server 2012 R2. SMB 3.1.1 — the latest SMB protocol — was introduced with Windows 10 and Server 2016.

Is SMB Secure?
With attacks like WannaCry and NotPetya making the news in recent years, you may wonder if SMB is secure. Of course, as with most network protocols, whether or not SMB is secure depends on your version and implementation. Generally speaking, SMB today is a highly secure protocol. For modern SMB implementations, here are some key takeaways for securing SMB:
1. Do NOT use SMBv1. SMB1 lacks encryption, is inefficient, and has been exploited in the wild by ransomware attacks.
2. Prefer SMB3 or later whenever possible. Of the 3 major SMB versions, SMB3 — particularly SMB 3.1.1 — offers the most security. For example, SMB3’s secure dialect negotiation limits susceptibility to man-in-the-middle (MITM) attacks and SMB 3.1.1 uses secure and performant encryption algorithms like AES-128-GCM.
3. Restrict SMB access to trusted networks and clients. Only allowing connections from trusted LANs or clients and implementing tight network security policies for SMB access can greatly reduce your attack surface.
Note: SMB Servers and SMB Clients will use the latest version they BOTH support. Therefore, you must consider both the server and client SMB software when securing Server Message Block implementations.
Understanding SMB Features
There are four key areas to consider when discussing SMB’s feature set. They are:
Authentication- SMB implements both user-level and share-level authentication to restrict access to resources. First, an SMB client must authenticate to the SMB server to gain access to resources (this is user-level authentication). From there, the client can access all resources not protected by share-level authentication. If share-level authentication is active on an SMB share, clients must input another password to gain access.
Secure data transfer- Message signing and encryption ensure the integrity and privacy of SMB data transferred across networks. One of the reasons using SMB3 is so important is because it offers the most benefits in this area, including modern encryption algorithms.
Performance- Throughput is vital to a good user experience. To enable usability, Server Message Block offers a variety of performance-enhancing features. For example, SMB Direct and Remote Direct Memory Access (RDMA) improves speed and efficiency in clustered environments.
Reliability- Features in this category deal with scalability, availability, fault tolerance, and failover. Modern SMB versions have matured to support a variety of high-availability (HA) environments with features such as transparent failover and SOFS (scale-out file servers).
Finding the right SMB client and server software
Finding the right SMB client and server software for your application will depend on your deployment model. Embedded systems and IoT devices have different requirements than data centers or corporate networks. However, there are several key factors to consider that apply across the board. Let’s take a look at two popular SMB software providers and see how they stack up against one another.
Samba vs Visuality Systems: Comparing the popular SMB software options
In non-Windows environments, two of the most popular choices for SMB client and server software are the open-source GPL v3 Samba and commercial solutions from Visuality Systems.
Portability and flexibility
Samba is supported across a variety of *nix operating systems. In addition to strong Linux and Unix support, Visuality Systems supports a wide variety of other platforms including Windows, iOS, Java platforms, and real-time operating systems (RTOS) such as ThreadX and VxWorks. Further, Visuality Systems takes a customer-driven approach to developing new on-demand features, making their Server Message Block solutions the most flexible on the market.
Licensing
Samba uses a “copyleft” license (GPL v3) that can create licensing conflicts and legal issues in commercial products. Visuality Systems offers OEM-friendly commercial licensing and SMB Microsoft Patents included in the license agreement (no need to contact Microsoft!).
Vendor support
Users in need of commercial support for Samba must contract with a 3rd party vendor. Visuality Systems supports their SMB software directly via an online helpdesk.
Tal Widerman, CEO, Visuality Systems