Introduction
As part of Microsoft’s Secure Future Initiative, launched in 2023 to address the growing scale and complexity of cyberattacks, Windows 11 version 24H2 and Windows Server 2025 now include important SMB security measures that enhance the safety of your data, users, and organization. Most of these features, supported by Visuality Systems’ SMB protocol software libraries, are enabled by default, ensuring a secure network setup from the start. One of the most critical security measures introduced in this update is SMB signing. For a deeper dive into this topic, we invite you to watch our video tutorial on SMB signing.
What is SMB Signing?
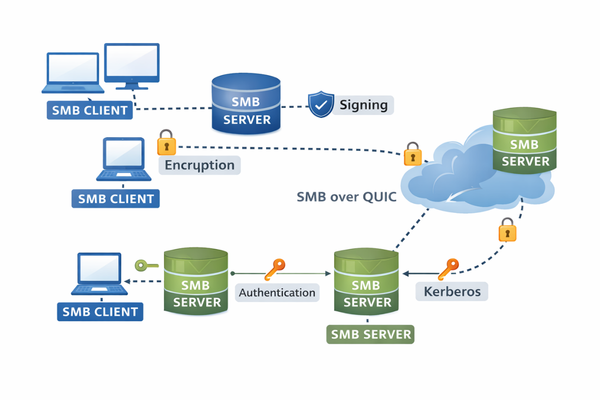
SMB signing adds a cryptographic signature to SMB messages, embedding it in the SMB header. This signature is generated using a hash derived from the session key and a cipher suite. If a message is intercepted or tampered with, the hash verification will fail, alerting the system to a potential security threat.
Key Benefits of SMB Signing
- Data Integrity – Confirms that the transmitted data has not been altered during transit.
- Authentication – Validates the identity of both the sender and receiver, blocking adversary-in-the-middle attacks.
So this mechanism ensures that SMB communication is both authentic and tamper-proof, providing a robust layer of defense for your organization.
SMB Signing Algorithms: A Journey Toward Stronger Security
Since its introduction in Windows NT, SMB signing has undergone significant enhancements:
- SMB1 – Relied on the now-outdated MD5 algorithm.
- SMB2 – Upgraded to HMAC-SHA-256, offering stronger cryptographic protection.
- SMB3 – Introduced AES-CMAC, further enhancing security.
Windows 11 & Server 2022 added AES-128-GMAC, the most robust signing algorithm to date to contrast modern threats.
SMB Signing: Before the Change
Previously, SMB signing was not enabled by default in many scenarios:
- Selective Enforcement – signing was required only for critical features like SYSVOL and NETLOGON, or if enforced by an Active Directory domain controller.
- Guest Access Vulnerability – devices using guest access had SMB signing disabled, leaving them exposed to potential threats.
- Administrator-Driven Enablement – only experienced administrators who understood its importance would configure SMB signing across networks, resulting in inconsistent adoption.
These gaps left networks vulnerable to attacks, particularly on less-secure devices and configurations.
SMB Signing: After the Change
The latest updates in Windows 11 and Windows Server 2025 address these vulnerabilities head-on:
- Enabled by Default – SMB signing is now mandatory across all supported configurations. Disabling it requires an explicit opt-out.
- Secure Connections Prioritized – Guest access and devices that lack SMB signing support are no longer permitted to connect without errors.
- Streamlined Security – Secure defaults ensure that organizations are protected even without extensive manual configuration.
These changes elevate SMB signing from an optional feature to a foundational security measure.
Configuring SMB Signing
Anyone can check and configure SMB signing using PowerShell. To check signing status run:
>\ Get-SmbClientConfiguration | FL RequireSecuritySignature
If you get a False, SMB signing is not enabled. To enable signing use the following command:
>\ Set-SmbClientConfiguration -RequireSecuritySignature $true
SmbClientConfiguration enforces signing for outbound connections. For inbound connections, use SmbServerConfiguration instead.
Best Practices & Common Pitfalls
Dos
- Use Kerberos: Leverage Kerberos instead of NTLMv2 for secure authentication in domain environments.
- Audit Network Activity: Regularly monitor SMB logons to detect and address potential vulnerabilities.
Don’ts
- Avoid Disabling Signing: Never disable SMB signing as a quick workaround—it compromises your network’s integrity.
- No Guest Accounts: Refrain from using guest accounts, which bypass critical security mechanisms.
- Don’t Use IP Addresses: Always connect using fully qualified domain names to ensure proper authentication and signing.
Conclusion
SMB signing is a cornerstone of secure SMB communication, ensuring the integrity and authenticity of your data. With Microsoft’s latest updates, this feature is now more robust and easier to implement than ever.
Visuality Systems offers SMB solutions fully aligned with Microsoft’s security measures. Our software libraries are designed to seamlessly support these enhancements, providing you with a secure and reliable foundation for your network. For tailored guidance or to learn more about how our solutions can strengthen your SMB implementation, don’t hesitate to contact us.
Raphael Barki, Head of Marketing, Visuality Systems