SMB Protocol Explained
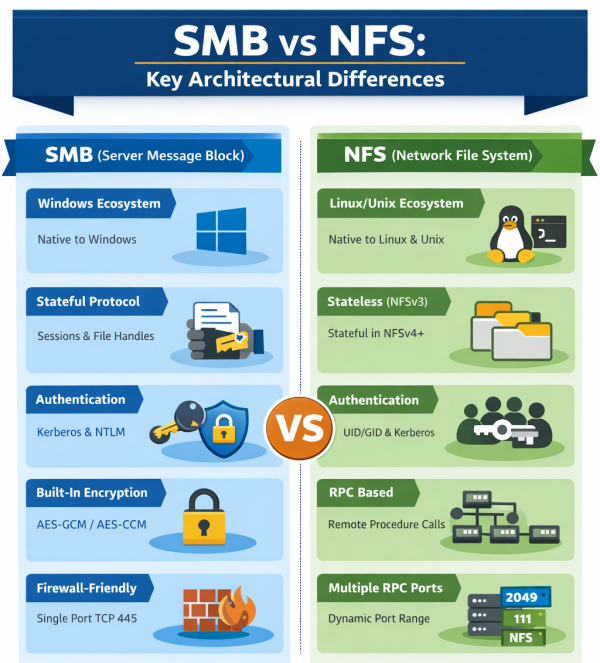
SMB and NFS are mature, widely deployed, and actively maintained protocols. Each aligns naturally with different operating system ecosystems and identity models. In hybrid and multi-OS environments, supporting both protocols is not optional but necessary.
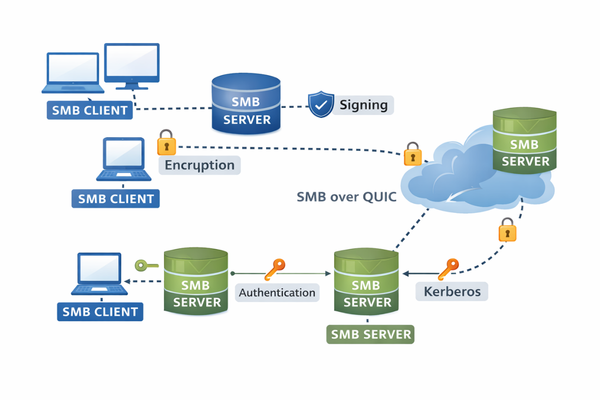
Understanding the distinct roles of the SMB client and SMB server is essential for architects, developers, and security professionals designing secure and reliable systems in enterprise and embedded environments.

ShareArchiver’s data management engine interacts with various file servers including Nutanix. This interoperability ensures ShareArchiver’s archiving solution works seamlessly across environments where SMB protocol is the only viable option for accessing and migrating data.

Switching from open-source SMB to Visuality Systems’ jNQ, a global pharma leader modernized its Java-based file transfer, achieving enterprise-grade security and long-term support.

By integrating YNQ, a leading CPE manufacturer enabled telco carriers to deliver value-added storage services, now deployed in over 15 million units.

After Seeburger gained some experience with an open source SMB library, a growing customer base demanded a more robust solution. This was the main driver to look for an independent implementation of SMB3 library, like Visuality Systems’ jNQ.

Metrohm chose Visuality Systems to upgrade existing connections from SMB1 to SMB3 with fully supported software libraries, without changing the application.

If your SMB-enabled Java application is still scanning directories to detect changes, you’re likely consuming more resources than necessary. SMB Notify is the right way to track file system updates and it’s supported by jNQ’s Java SMB stack.

Cryptic exceptions and tricky platform differences are common when trying to integrate SMB file sharing into a Java application. What are the most common roadblocks? How can you work around them?

